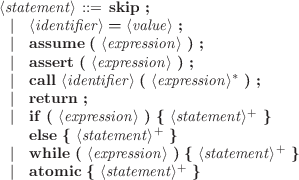
c2s was implemented in Haskell. Here are binaries for Linux:
| 32-bit Linux distribution /x86 | : | c2s-v0.1-linux-32.tar.gz |
| 64-bit Linux distribution /x64 | : | c2s-v0.1-linux-64.tar.gz |
The building blocks of concurrent programs are processes, procedures and statements. The grammar of statements is given in Figure 1. They consist of simple C-like statements, enriched with nop , assume , assert and atomic . We assume that assignments are atomic. For simplicity, the grammar rules out nested function calls, e.g. a = f(g(h(b)));.
A procedure consists of a sequence of arguments, a set of local variables, and a sequence of statements. A process is composed of a finite set of global variables and a finite sequence of procedures. For each process, the first procedure in the sequence constitutes the entry point. Our code-to-code transformation deals only with boolean and integer types of variables. Variables of both types can be set to non-deterministic values using the following syntax:
In Figure 3 we show the Dekker mutual exclusion algorithm written in our language.
Our tool should be used as a command line:
./c2s --src=filename1 --dest=fileneame2 --syntax=OutSyntax -k kval [-n nval]
Where:
./c2s --src=dekker.code --dest=dekker.c --syntax=CPROVER -k 0
To verify the generated code, you can invoke Cbmc using:
./cbmc dekker.c --unwind 14 --16
The --unwind n Cbmc option unwinds loops n times in the program being verified. The --16 defines integer size in bits.
./c2s --src=dekker.code --dest=dekker.c --syntax=CPROVER -k 0
To verify the generated code, you can invoke Esbmc using:
./esbmc dekker.c --unwind 14
The --unwind n Esbmc option unwinds loops n times in the program being verified.
./c2s --src=dekker.code --dest=dekker.rem --syntax=REMOPLA -k 0 -n 2
The integer size here is 2 since in Dekker integer variables do not go above 1, so 22 - 1 = 3 is acceptable as an upper bound. To verify the generated code, you can invoke Moped using:
./moped dekker.rem error
The experiments were ran on a 2.2 GHz Intel Core i7 with 4 GB of memory using Moped 2.0, CBMC 4.0, ESBMC 1.18 and Poirot 1.0 [4]. All the files (including some scipts for translating and running the tools) can be downloaded here. The operating systems used were Ubuntu (32-bit) and Windows 7 (32-bit).
| Type of Analysis
| |||||||||||||
| Concurrent to Sequential | Concurrent
| ||||||||||||
| Examples | k
1 | Moped | Cbmc | Esbmc | k2 | Poirot | k3 | Esbmc | |||||
| Account | 0 | -. | - | -. | - | 1. | 1 | 4 | 3. | 34 | 10 | -. | - |
| BigNum | 0 | 8. | 39 | -. | - | -. | - | 26 | -. | - | 234 | -. | - |
| Bluetooth3a | 0 | 744. | 49 | -. | - | -. | - | 11 | 18. | 38 | 28 | FP | |
| Token Ring | 0 | 0. | 13 | 0. | 2 | 0. | 18 | 1 | 2. | 72 | 4 | 1. | 47 |
| Account Bad | 0 | -. | - | 0. | 48 | 1. | 41 | 1 | 2. | 13 | 4 | 0. | 11 |
| BigNum Bad | 0 | 5. | 9 | 13. | 4 | 239. | 4 | 26 | -. | - | 26 | -. | - |
| Bluetooth1 | 1 | 4. | 18 | 0. | 37 | 1. | 28 | 2 | 1. | 92 | 5 | NF | |
| Bluetooth2 | 1 | 0. | 64 | 5. | 68 | 34. | 38 | 3 | 2. | 9 | 5 | 0. | 5 |
| Bluetooth3b | 1 | 1. | 26 | 0. | 95 | 5. | 0 | 2 | 2. | 5 | 5 | NF | |
| Infinite Loop 1 | 1 | 4. | 1 | 0. | 2 | 0. | 25 | 2 | 1. | 45 | 1 | 0. | 08 |
| Infinite Loop 2 | 1 | 17. | 3 | 0. | 84 | 3. | 85 | 1 | 0. | 96 | 1 | 0. | 09 |
| Token Ring Bad | 0 | 0. | 13 | 0. | 16 | 0. | 26 | 2 | 2. | 74 | 4 | 0. | 27 |
[1] Moped home page: http://www.fmi.uni-stuttgart.de/szs/tools/moped/.
[2] Cbmc home page: http://www.cprover.org/cbmc/.
[3] Esbmc home page: http://esbmc.org/.
[4] Poirot home page: http://research.microsoft.com/en-us/projects/poirot.