Experimental Archaeology in Digital Computing
Hacking 36 Bits at a Time
Björn Victor
Uppsala University (1985-)/Update (1983-)
Experimental Archaeology?
What do the archaeological artifacts (e.g. stone chips, bronze fragments) mean? What were they used for, and how?
- To find out: experimental archaeology:
-
 reconstruct and recreate conditions, tools, equipment etc
to test, evaluate and explicate method, technique, assumption,
hypothesis and theories.
reconstruct and recreate conditions, tools, equipment etc
to test, evaluate and explicate method, technique, assumption,
hypothesis and theories.
- i.e: to see if and how it worked.
Example: Heyerdahl's Kon-Tiki and Ra travels (S. America-Polynesia, Egypt-S.Am).
What has this got to do with NUCCC?
...in Digital Computing
 DEC: Digital Equipment Corporation, Maynard, Massachusetts.
DEC: Digital Equipment Corporation, Maynard, Massachusetts.
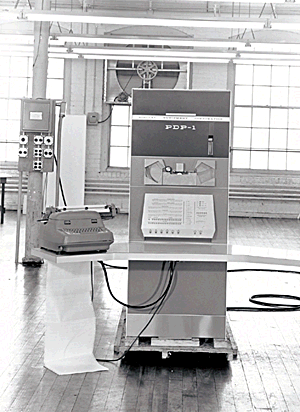
- Start: 1957
-
First computer 1960: the PDP-1 (Programmed Data Processor)
- timesharing OS 1962, 18-bit architecture, first videogame
-
Other well-known PDPs:
- PDP-8 (1965): world's first mass-produced minicomputer (12-bit)
- PDP-11 (1970-1990?): extremely common (16-bit)
- Also known for VAX (1977-1992), VT100 terminals (1978-), Alpha (1992)...
- Bought by COMPAQ in 1998.
36 Bits at a Time

First DEC 36-bit machine: PDP-6 (1964), followed by the PDP-10 in 1967.
-
Four major variants:
- KA-10 (1967)
- KI-10 (1972): integrated circuits!
- KL-10 (1974): "low cost" (~400KE, ECL)
- KS-10 (1978): "small"
-
 Clones: e.g.
Clones: e.g.
Foonly (used for the TRON movie CG);
SC-20/30/40 (ca 1985);
XKL Toad-1 (199x)
PDP-10: Architectural basics
- 36-bit words
- Microcoded (2k 75-bit words); 22-bit physical addresses; 8 register banks of 16 registers
- Up to 4 MW memory (18 MB), up to 4 KW cache (KS: 0.5 MW/0.5KW)
-
Virtual memory:
- non-KL systems:
18 bits = 512 pages of 512 words - KL ("extended addressing"):
23 bits = 32 "sections" of 512 pages
- non-KL systems:
- KL: PDP-11 frontend (terminals, printers, etc) (KS: 8080)
- Peripherals through Massbus, Unibus, CI (HSC)
- Disk examples: RP06 (176 MB), RP07 (498 MB)
Instruction format
Instruction format by example:
- 1. Calculate effective address
- FOO: 18-bit (right halfword)
- (3): index by contents of register 3
- @: indirect addressing - "recurse" at that address (using indexing and indirection, until not indirect)
- 2. then execute instruction MOVEI
- move Immediate (use the effective address, not contents) to register 2
Logically grouped instruction set
- Move a word
-
MOV[ESNM]{I,M,S}? register, address
- [ESNM] E: standard; S: swapped; N: negate; M: magnitude
- {I,M,S} I: immediate; M: reg to memory; S: to self
- Halfword move
-
H[RL][RL]{Z,O,E}?{I,M,S}? register, address
- {Right,Left}-to-{Right,Left} and {Zero,Ones,Extend} to other half
- Logical test and modification
-
T[RLDS][NZCO]{E,A,N}? register, address
- Test {Right,Left,Direct,Swapped} mask, {No,Zeros,Complement,Ones} modification, and skip if bits {Equal,Always,Not equal} to zero
- Ex: MOVS 2,FOO - swaps content of FOO and moves to reg 2
- Ex: HRLZM 2,BAR - moves RH(2) to LH(BAR), zeroes RH(BAR)
- Ex: TLCE 2,700 - test if LH(2) has 700 bits set, complement them, and skip if zero
Other instructions
Some more instruction examples:
- Shift/rotate (LSH, ASH, ROT)
-
Iteration (AOBJN)
-
add one to both halfwords, jump if negative:
DO-WHILE: set up -count,,0 in register, do body, then AOBJN reg,TOP
-
add one to both halfwords, jump if negative:
-
Stack (PUSH, POP)
- Stack pointer: -length,,top
-
Call (PUSHJ, POPJ)
- push PC and jump/jump to popped address
-
Byte fields (LDB, DPB)
- load/deposit n-bit byte using byte pointer
Experiments: operating systems
Historical perspective
- TOPS-20
- Released 1976 - last DEC version 1988
- Historical: good documentation, experience of original system
Archaeological perspective
- ITS - the Incompatible Timesharing System
- Developed at MIT for PDP-6, then for PDP-10
- Archaeological: less documentation, few people with real experience
TOPS-20

Features:
- User friendly: the "shell" (EXEC) with command completion, interactive help...
- File system: versions, deleted/undeleted, offline files/migration, relatively fine-grained protection
- Jobs, processes, subprocesses, IPC, shared memory
- OS kernel (monitor): paging, working set scheduler, copy-on-write, relatively fine-grained privileges
Misfeatures(?)
- OS written in assembly (powerful assembler)
powerful macros: subroutines with args, local variables, ...
TOPS-20: Interactive experiments
It's safe to try this at home!
- Telnet to TINA.UPDATE.UU.SE
- Explore: try typing "?" everywhere, use ⟨Esc⟩ for command completion.
- Username GUEST, password xxxx
- Exercise: find out filename syntax. (Hint: use EMACS.)
ITS (from the New Hacker's Dictionary)
-
Incompatible Time-sharing System, an influential though highly
idiosyncratic operating system written for PDP-6s and PDP-10s at
MIT and long used at the MIT AI Lab.
...
ITS pioneered many important innovations, including transparent file sharing between machines and terminal-independent I/O.... -
A mythical image of operating-system perfection worshiped by a
bizarre, fervent retro-cult of old-time hackers and ex-users....
ITS worshipers manage somehow to continue believing that an OS maintained by assembly-language hand-hacking that supported only monocase 6-character filenames in one directory per account remains superior to today's state of commercial art...
ITS: Incompatible Timesharing System
Developed at MIT: 196x - 1982/1990. Origin of EMACS.
-
ITS is a truly open system:
- No file protection
- - so anyone can fix bugs (+ file versions)
- Little process protection
- - so users can help eachother debug
- Little system protection
- - no incentive to "break the system"
- Originally no passwords (or even user definition!)
- File system: 6+6-char filenames, flat directories, versions, links, network transparency
- Networking: CHAOSnet (early Ethernet, pre-TCP/IP) and TCP/IP via IMP (Arpanet, pre-Internet)
ITS: Interactive experiments
Try it!
- Download http://victor.se/bjorn/its/supdup-jta25.jar
- Connect with
java -jar supdup-jta25.jar
Select "Connect", enter up.update.uu.se - Explore: try typing "?" or :HELP
- Username GUEST, password xxxx
- Exercise: read my mail.
- Bonus exercise: use :SUPDUP MD to connect to a completely open ITS system.
See http://victor.se/bjorn/its/luser.php for cheat codes.
Emulating the PDP-10
Questions when emulating old systems:
-
What needs to be emulated?
- instructions, memory, ...
-
How do you find out how to?
- processor reference manual, ...
-
How good are the specifications and documentation?
- Usually natural language - ambiguous, imprecise, and incomplete
- Even microcode sources don't help for everything
-
How faithful does the emulation need to be?
- run original unmodified software
- timing? bug-bug compatibility?
- "Experimental archaeology" needed -
- try and see what works, and/or if it works.
The KLH10 emulator
KLH10: The best available PDP-10 emulator (cf. e.g. simh, kx10).
- Developed by Ken L. Harrenstien, ca 1990/2001
- Processor: KN10 (KS, KL versions)
- Device processes: disks, magtapes, network (asynchronous)
- Faithful and complete (except some things...)
- Minimising load on host system: new device used by scheduler
-
Portable (Linux, Solaris, NetBSD, MacOS, ...)
- e.g. various representations of 36 bits on 32/64-bit machines
- networking may need hacking
Archaeological experience
Some of my experience as experimental archaeologist:
-
Instructions ("microcode") for an earlier emulator, KX10.
- Informal specification
- No real KL10 to try on (but clones)
-
Adapting network emulation to Solaris/Linux
- Linux is simpler
-
Unibus CHAOSnet interface for KN10-KS (for ITS).
- No specification
- No real hardware
- No live experience
- Indirect spec: ITS sources using the interface
- Archaeological finds(!) may help
and lots of fun!
Conclusion
Some random conclusions:
-
History of computing is (too) often forgotten.
- Why do present OSs work like they do?
-
Old features take a long time to be re-invented.
- Why has Linux/Unix still (basically) only root privs?
- Why do command interfaces still suck?
- If you like low-level hacking but not hardware hacking, try an emulator.
-
Document your software and specify your hardware
- you can't judge the future interest in advance.
Play at home: check out http://www.aracnet.com/~healyzh/pdp10emu.html, http://victor.se/bjorn/its